
Shadowserver’s New Public Dashboard
Thanks to the generous support of the UK Foreign, Commonwealth & Development Office (FCDO), Shadowserver Team sannounce the launch of the new Shadowserver Public Dashboard:https://dashboard.shadowserver.org The new Dashboard lets you explore some of the many...

MISP GUARD
Let’s say that by no means should an attribute of type passport-number leave your MISP instance. Aside from the analyst following best practices when encoding the data, MISP does not have a built-in mechanism to prevent these leaks to happen, but now you can achieve...

Ransomware Group Uses Recycled Code
A new ransomware group, called Monti, appears to have used leaked Conti code, TTPs, and infrastructure approaches to launch its own ransomware campaign. Analysts have discovered a ransomware campaign from a new group called "Monti," which relies almost entirely on...

OpenCTI upgrade: data sharing capabilities
The figure below represents the current landscape of OpenCTI sharing capabilities. OpenCTI data sharing landscape What’s new in OpenCTI 5.3.x? Menu reorganization As data sharing features are increasing, we refactored a bit the menu to group these...

What a Successful Threat-Hunting Program Looks Like?
Threat hunters can help build defenses as they work with offensive security teams to identify potential threats and build stronger threat barriers. Over the last few years, an influx of high-profile industry security issues (PDF) have placed offensive tactics among...
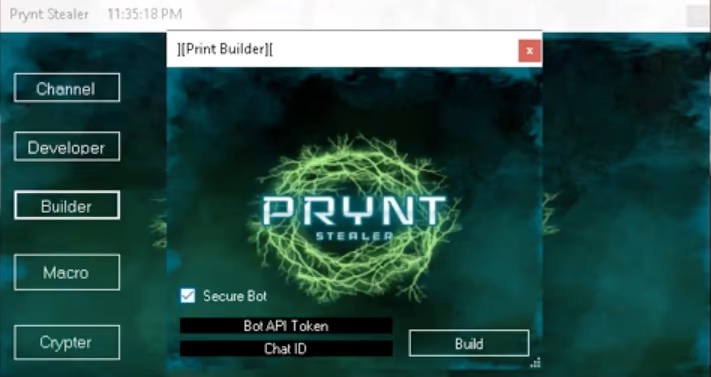
Malware steal data from other hackers
Cybercriminals using Prynt Stealer to collect data from victims are being swindled by the malware developer, who also receives a copy of the info over Telegram messaging service. The malware developer has planted in the builder for the infostealer a backdoor that is...

How to protect against fraud?
2022 has so far seen an insatiable appetite for stories of fraud From ‘The Tinder Swindler’ Simon Leviev fooling potential love interests into giving him millions of dollars to escape his “enemies”, to con artist Anna Delvey winning the hearts and purses of New York’s...

Nearly 3 Years Later, SolarWinds CISO Shares 3 Lessons From the Infamous Attack
SolarWinds CISO Tim Brown explains how organizations can prepare for eventualities like the nation-state attack on his company’s software. On Dec. 8, 2020, FireEye announced the discovery of a breach in the SolarWinds Orion software while it investigated a...

Microsoft: Russian malware hijacks ADFS to log in as anyone in Windows
Microsoft has discovered a new malware used by the Russian hacker group APT29 (a.k.a. NOBELIUM, Cozy Bear) that enables authentication as anyone in a compromised network. As a state-sponsored cyberespionage actor, APT29 employs the new capability to hide their...
