
LastPass developer systems hacked to steal source code
Password management firm LastPass was hacked two weeks ago, enabling threat actors to steal the company's source code and proprietary technical information. The disclosure comes after BleepingComputer learned of the breach from insiders last week and reached out to...

The top three learnings from the 2022 Verizon Data Breach Incident Report
The data displayed in the new Verizon Data Breach Incident Report (DBIR) offers critical insight into the current state of cybersecurity After a year of data breaches and cyberattacks consistently dominating headlines, this year’s report closely examines what...

Hackers target hotel and travel companies with fake reservations
A hacker tracked as TA558 has upped their activity this year, running phishing campaigns that target multiple hotels and firms in the hospitality and travel space. The threat actor uses a set of 15 distinct malware families, usually remote access trojans (RATs), to...

Patch Now: 2 Apple Zero-Days Exploited in Wild
The fact that the flaws enable remote code execution, exist across all major Apple OS technologies, and are being actively exploited heightens the need for a quick response. Security researchers are urging users of Apple Mac, iPhone, and iPad devices to immediately...

The Hacking of Starlink Terminals Has Begun
It cost a researcher only $25 worth of parts to create a tool that allows custom code to run on the satellite dishes. SINCE 2018, ELON Musk’s Starlink has launched more than 3,000 small satellites into orbit. This satellite network beams internet connections to...
Discovering Domains via a Time-Correlation Attack on Certificate Transparency
Many modern websites employ an automatic issuance and renewal of TLS certificates. For enterprises, there are DigiCert services. For everyone else, there are free services such as Let’s Encrypt and ZeroSSL. There is a flaw in a way that deployment of TLS certificates...
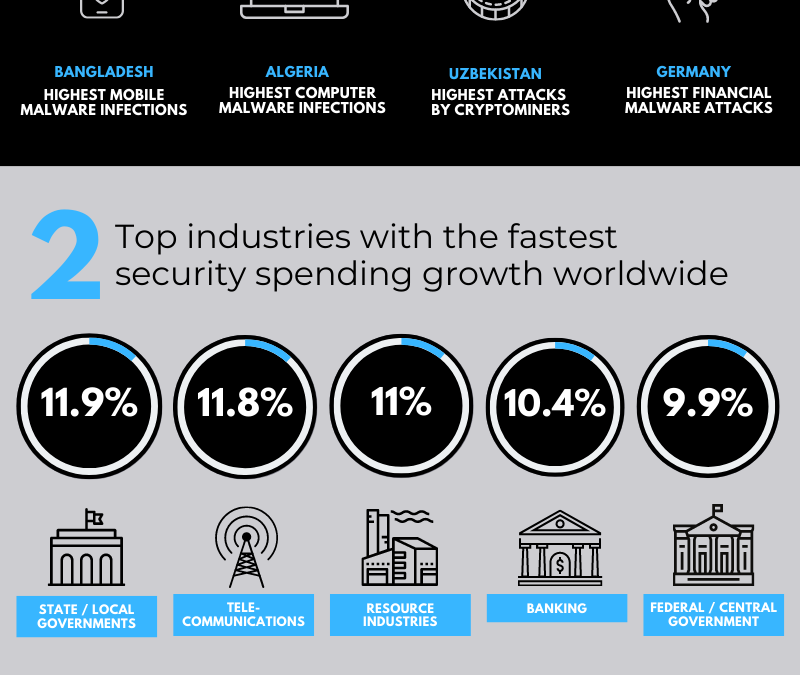
Top 3 CyberSecurity Statistics You Must Know

Incident Response and its Best Practices Using Wazuh
Digital security for the business sector and enterprises is crucial. Keeping this in view, 2021 was marked by cyberattacks and major data breaches. Not just that, also ransomware has emerged as a major role in the cyber community. Wazuh is an open-source security...
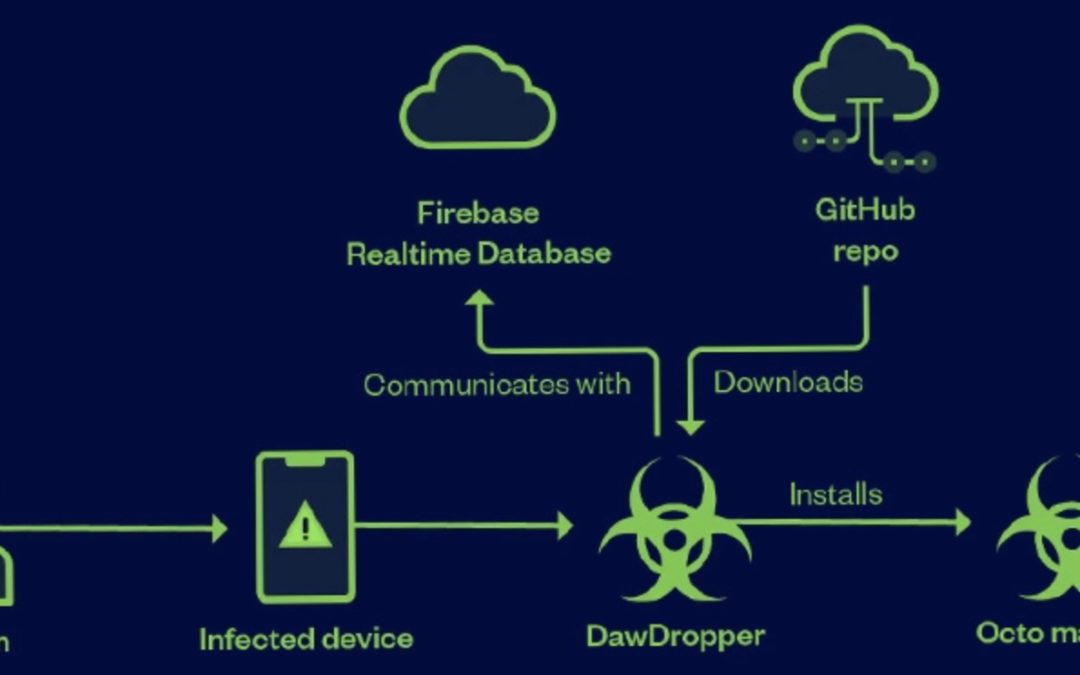
Over a Dozen Android Apps on Google Play Store Caught Dropping Banking Malware
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such...
