
In the ever-evolving landscape of cyber threats, a notorious Iranian-sponsored cyber actor known as OilRig, or APT34, has once again made its presence felt. This time, the group has orchestrated a spear-phishing campaign, unleashing a new strain of malware named Menorah. The malware, tailor-made for cyber espionage, exhibits a formidable set of capabilities, including machine identification, file reading and uploading, and downloading additional files or malware.
Understanding Menorah Malware and its Capabilities
Menorah malware represents a significant advancement in cyber weaponry, designed to infiltrate and compromise targeted machines with precision. Its ability to identify, read, and upload files from the victim’s system, coupled with the potential to download additional malicious payloads, marks a new level of sophistication. This places Menorah in the category of advanced malware that poses a substantial threat to cybersecurity.
The Victims: Cloaked in Mystery
While the exact identities of the victims remain undisclosed, indicators within the campaign suggest that at least one target is an organization based in Saudi Arabia. The deployment of decoys adds another layer of complexity to discerning the true targets, emphasizing the covert and strategic nature of the attacks orchestrated by OilRig.
OilRig: APT Group Extraordinaire
OilRig, also known by its aliases such as APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten, stands as a prominent Iranian APT group specializing in covert intelligence gathering operations. Their expertise lies in infiltrating and persisting within targeted networks, with a primary focus on espionage. Over the years, they have honed their craft, executing high-profile cyberattacks across the Middle East. Their range of targets spans from government agencies to critical infrastructure and regional entities, showcasing the extent of their ambitions and capabilities.
Continuous Evolution: The OilRig Way
Recent discoveries from NSFOCUS have shed light on OilRig’s continual development and evolution in tactics and malware. The unveiling of a new variant of the SideTwist malware in a recent phishing attack is a testament to their ongoing refinement and sophistication. The adaptability of OilRig showcases their ability to experiment with routines and techniques, ensuring optimal effectiveness in their cyber campaigns.
Unraveling the Infection Chain: Menorah Malware at Work
The modus operandi of the Menorah malware begins with a lure document strategically designed to establish persistence. Through a scheduled task and the deployment of the “Menorah.exe” executable, the malware gains a foothold in the compromised system. Subsequently, the executable establishes communication with a remote server, awaiting further instructions. The malware, constructed on the .NET platform, boasts a rich feature set, encompassing critical functions such as host fingerprinting, file operations, shell command execution, and more.
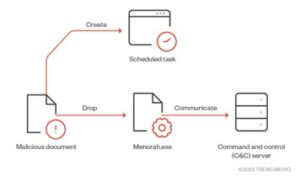
Source: https://www.trendmicro.com/en_us/research/23/i/apt34-deploys-phishing-attack-with-new-malware.html
A Call for Enhanced Cybersecurity Measures
In a landscape where cyber threats continue to evolve and proliferate, it is imperative for organizations to prioritize cybersecurity. Proactive measures, including continuous employee education about diverse attack techniques, are paramount. Fostering a culture of heightened cybersecurity awareness is critical to fortify defenses against potential cyber threats. The ability to swiftly adapt to emerging threats is fundamental in safeguarding critical assets and maintaining a resilient security posture.
Here are the recommended measures to prevent similar incidents
Keep Systems and Software Updated:
Ensure that all software, operating systems, and applications are consistently updated with the latest security patches and updates. Regularly monitor and install security updates promptly.
Strengthen Access Controls:
Enforce robust authentication methods, such as multi-factor authentication (MFA), to secure access to critical systems and sensitive data. Limit access according to the principle of least privilege (PoLP).
Provide Employee Education and Training:
Conduct regular cybersecurity awareness training for all employees to educate them about phishing attacks, social engineering, and best practices for online safety. Encourage employees to remain vigilant and promptly report any suspicious activities.
Sources
https://www.darkreading.com/dr-global/iran-linked-apt34-spy-campaign-targets-saudis
https://www.trendmicro.com/en_us/research/23/i/apt34-deploys-phishing-attack-with-new-malware.html
https://thehackernews.com/2023/09/iranian-apt-group-oilrig-using-new.html
https://vulners.com/thn/THN:313700ECB7236AFF53139579B5EED13D
https://malware.news/t/new-menorah-malware-bolsters-oilrig-apts-cyberespionage-efforts/74076
https://www.cyclonis.com/menorah-malware-employed-by-iranian-apt/
Akos Sipos
(UPS student)
