
by Tibor Luter | Mar 2, 2021 | blog
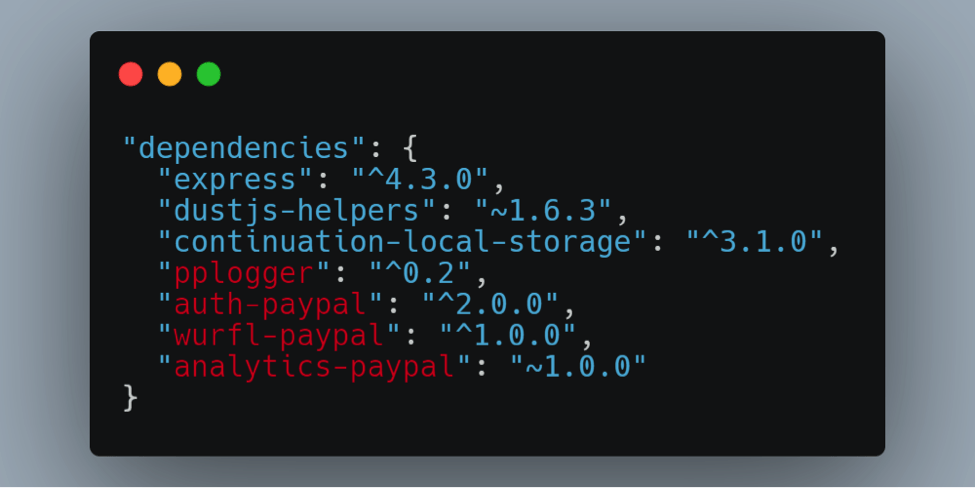
New ‘dependency confusion’ attack technique recognized by Microsoft New “dependency confusion” technique, also known as a “substitution attack,” allows threat actors to sneak malicious code inside private code repositories by...

by Tibor Luter | Dec 16, 2020 | blog
CISOs Preparing for DNS Attacks Over Christmas Just over three-quarters of cybersecurity professionals have said they expect to see an increase in DNS-related security threats over the next few weeks. In preparation, three in five (59%) have altered their DNS security...

by Tibor Luter | Dec 16, 2020 | blog
Employees 85% more likely to leak files today vs pre-COVID The company is rolling out a patch for the vulnerabilities, which allowed one researcher to break into a car in 90 seconds and drive away. Employees are 85 percent more likely today to leak files than they...

by Tibor Luter | Nov 30, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] Hackers are putting a bullseye on healthcare. Experts explore why hospitals are...

by Tibor Luter | Nov 16, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] A tanfolyam célja A tanfolyam célja olyan mélyebb technológiai ismereteket...






Recent Comments