
by Tibor Luter | Sep 15, 2022 | blog
Let’s say that by no means should an attribute of type passport-number leave your MISP instance. Aside from the analyst following best practices when encoding the data, MISP does not have a built-in mechanism to prevent these leaks to happen, but now you can achieve...

by Tibor Luter | Sep 14, 2022 | blog
A new ransomware group, called Monti, appears to have used leaked Conti code, TTPs, and infrastructure approaches to launch its own ransomware campaign. Analysts have discovered a ransomware campaign from a new group called “Monti,” which relies almost...

by Tibor Luter | Sep 12, 2022 | blog
The figure below represents the current landscape of OpenCTI sharing capabilities. OpenCTI data sharing landscape What’s new in OpenCTI 5.3.x? Menu reorganization As data sharing features are increasing, we refactored a bit the menu to group these...

by Tibor Luter | Sep 7, 2022 | blog
Threat hunters can help build defenses as they work with offensive security teams to identify potential threats and build stronger threat barriers. Over the last few years, an influx of high-profile industry security issues (PDF) have placed offensive tactics among...

by Tibor Luter | Sep 5, 2022 | blog
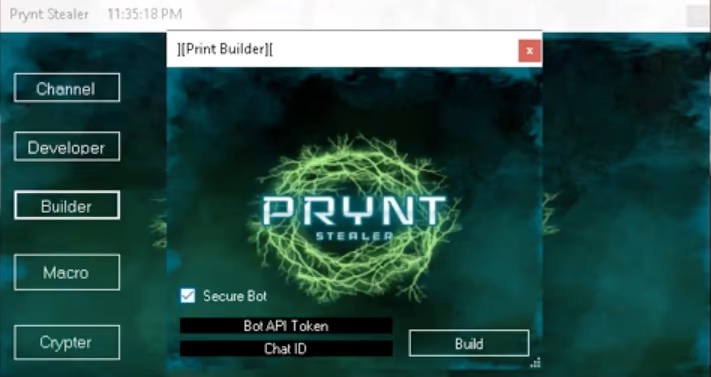
Cybercriminals using Prynt Stealer to collect data from victims are being swindled by the malware developer, who also receives a copy of the info over Telegram messaging service. The malware developer has planted in the builder for the infostealer a backdoor that is...






Recent Comments