
by Tibor Luter | Aug 30, 2024 | Fusion Center, Luter
In today’s blog post, we will be going over a tool that is a must-have in every security analyst’s arsenal. Even if you won’t use it every day, it is helpful to understand what malware signatures look like in the background. YARA is a powerful...

by Tibor Luter | Nov 28, 2022 | blog
Detecting and Fingerprinting Infostealer Malware-as-a-Service platforms Cyber threat intelligence largely involves the tracking and studying of the adversaries outside of your network. Gaining counterintelligence about your adversaries’ capabilities and weaponry...

by Tibor Luter | Sep 5, 2022 | blog
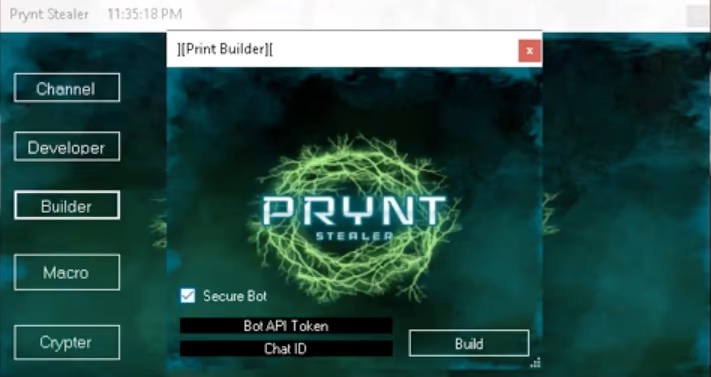
Cybercriminals using Prynt Stealer to collect data from victims are being swindled by the malware developer, who also receives a copy of the info over Telegram messaging service. The malware developer has planted in the builder for the infostealer a backdoor that is...

by Tibor Luter | Aug 31, 2022 | blog
SolarWinds CISO Tim Brown explains how organizations can prepare for eventualities like the nation-state attack on his company’s software. On Dec. 8, 2020, FireEye announced the discovery of a breach in the SolarWinds Orion software while it investigated a...

by Tibor Luter | Aug 29, 2022 | blog
Microsoft has discovered a new malware used by the Russian hacker group APT29 (a.k.a. NOBELIUM, Cozy Bear) that enables authentication as anyone in a compromised network. As a state-sponsored cyberespionage actor, APT29 employs the new capability to hide their...






Recent Comments