
by Tibor Luter | Aug 26, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] What is Shodan? Shodan is a search engine that finds devices and device types...

by Tibor Luter | Aug 25, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] Abstract When I published my first article, Attacking Azure & Azure AD and...

by Tibor Luter | Aug 25, 2020 | blog
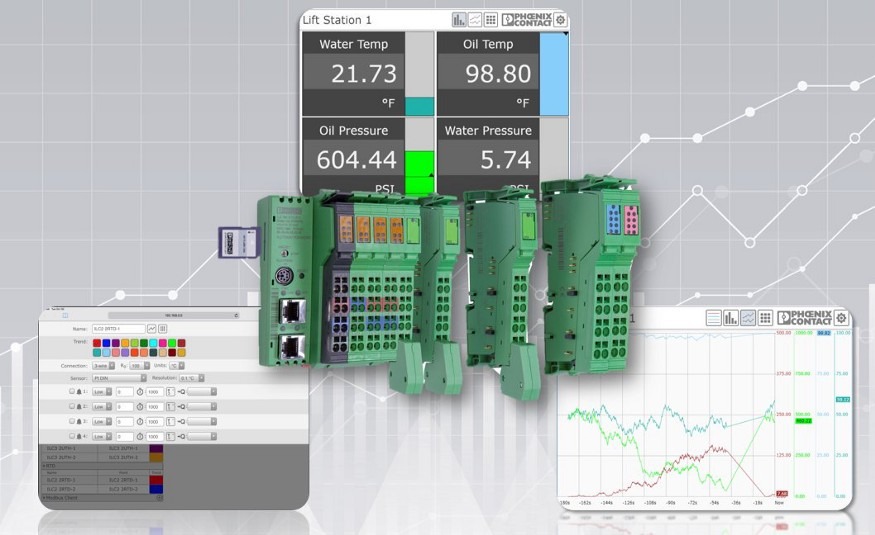
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] To date, most industrial process data is fed to proprietary SCADA systems that...

by Tibor Luter | Aug 22, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] Xstream architecture, DPI engine, and TLS inspection XG Firewall v18 MR1 is now...

by Tibor Luter | Aug 16, 2020 | blog
[vc_row][vc_column][vc_wp_text] [xyz-ips snippet=”metadatatitle”] [/vc_wp_text][vc_empty_space][/vc_column][/vc_row][vc_row][vc_column width=”2/3″][vc_column_text] Guardicore unveiled new capabilities for Infection Monkey, its free, open source...






Recent Comments